Physicians take all sorts of photographs. Some are part and parcel of a surgeon’s practice. Before and after photos of cosmetic surgery. For example. No surprises there.
Patients of Lehigh Valley Health Network were surprised that hackers obtained photos of their naked bodies while undergoing radiation treatment.
Hackers breached the network.
A Lehigh Valley Health spokesperson said the cyberattack was limited to a network supporting a single physician practice in Lackawanna County, in northeast Pennsylvania, and confirmed it did not pay a ransom. “Patient, physician and staff privacy is among our top priorities, and we continue to enhance our defenses to prevent incidents in the future,” he said.
It’s not clear precisely how much ransom was demanded. But it was more than $5M. The healthcare system refused. Pics ended up on the dark web.
The Health Network was sued in class action lawsuit.
“The pictures are really difficult to look at,” said Patrick Howard, an attorney representing the plaintiffs. His legal team hired a cybersecurity expert who located the images that hackers had posted on the dark web, enabling them to “establish each person’s information that was actually online.”
“The unidentified woman, who is in her 50s and known as Jane Doe, became the lead plaintiff in a class action suing Lehigh for failing to safeguard highly sensitive patient information, including nude photos of hundreds of cancer patients. On Sept. 12, a law firm announced that Lehigh had agreed to pay $65 million to settle the case.”
“The class-action lawsuit recounts how the executive offered an apology to the woman in her 50s and, “with a chuckle, two years of credit monitoring.” The cancer patient had no idea that the health system had stored nude photos of her on its computer network, according to the lawsuit, and was in a state of “complete disbelief.”
“Indeed, while LVHN is publicly patting itself on the back for standing-up to these hackers and refusing to meet their ransom demands, they are consciously and intentionally ignoring the real victims: Plaintiff and the Class. Rather than act in their patients’ best interest, LVHN put its own financial considerations first. L VHN must be held to account for the embarrassment and humiliation it has caused Plaintiff and the Class.”
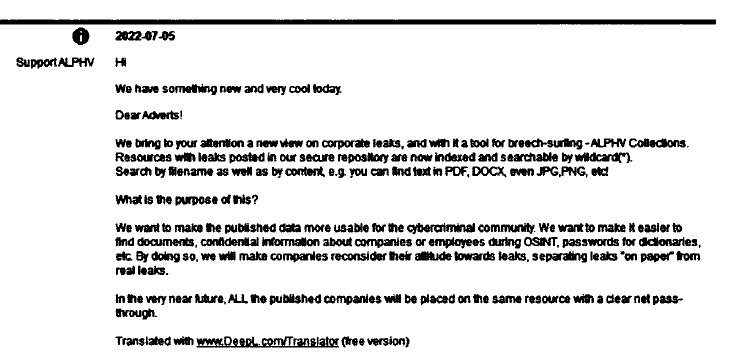
The lawsuit detailed the hack by an organization called ALPHV:
“ALPHV is also ruthless in its quest for ransom payments. In July 2022, ALPHV announced on Twitter that it was creating a searchable “repository” of data stolen from various companies in order to make it “more usable for the cybercriminal community.” The group made clear its purpose was to “make it easier to find documents, confidential information about companies and employees” and by doing so will “make companies reconsider attitude towards leaks[.]”
Drip, drip, drip.
“Yet, LVHN still refused to give into the hackers, and as a consequence on March 10, ALPHV uploaded an additional 132 gigabyte file onto the dark web, which the hackers described as containing additional patient data and photos. ALPHV promises to leak more patient data and images every week until the ransom is paid.”
How did this end?
A record $65 million settlement has been reached between class-action attorneys at Saltz Mongeluzzi Bendesky and Lehigh Valley Health Network (LVHN) in a case filed in March, 2023, on behalf of nearly 135,000 patients and employees of the health system, more than 600 of whom had their personal medical-record photos hacked and posted on the internet, according to the Firm.
The settlement in J. Doe v. Lehigh Valley Health Network, Lackawanna County Court of Common Pleas, No. 23-CV-1149, is believed to be the largest of its kind, on a per-patient basis, in a healthcare data breach-ransomware case.
The Court has scheduled a November 15, 2024 final fairness hearing to determine if the settlement should receive final approval. If approved, Mr. Howard and Mr. Paris estimate the settlement funds will be distributed early next year.
Those who have been notified they are in the class are not required to take any action to receive compensation. Every Settlement Class member, under the agreement, will receive payment, ranging from $50 to $70,000; those receiving the maximum had their hacked nude photos published online.
These are tough cases.
Practices must harden their hardware defenses against breaches. They must train employees to avoid becoming unwitting accomplices to breaches. And they must have cyberliability insurance which covers such threats.
What do you think?






Obviously I would not want any pictures of me or a loved one on the dark web. But only a limited number of people spend time and effort on the dark web. Those who do have a primary purpose of trying to find a way to score money off of it. Perhaps by blackmail or securing bank account information to pass forged checks from your account.
I would think that financial crimes would be of far greater “interest”than nude photos of some older person they do not know.
We had some bad checks for very large amounts written on our checking account. It sounds weird to say that I was far more “unhappy” about that than I would have been by a dark web “enthusiast” seeing me naked.
I might have even laughed over that. Older naked people who may have had surgery are just not particularly interesting. I guarantee that I am not!
I don’t think it is possible to guarantee that these things won’t happen. I think this is just one of the things we have to learn to live with. I am sorry some people were embarrassed. But I personally don’t care.
Michael M. Rosenblatt, DPM
Mike,
I would pay NOT to see the nude pictures of you on the internet!! In fact, I would give my Bank of America routing and account number to a hacker who agrees to the above!!
To be serious, these hospitals and large medical groups already have hardened systems and cybersecurity experts as consultants. They can afford the best. The smaller groups and solo practices certainly do not have this level of digital protection. Even the solo practice has the critical information of thousands of patients. That is certainly a target.
Penetration testing of any computer system is a must. And one must be mindful that one’s staffer, even the receptionist or a part time kid who is “helping out” can give the physician an overwhelming amount of grief
The best protection is to keep very sensitive information not on a computer system that can be penetrated. I had my clinical pictures and other sensitive information on personal files. Were my Chiefs happy with that? No. But that is what I was comfortable with.
And, I am a patient of a physician who still keep paper records and I know that this doctor has less exposure to breeches, but, it’s still a real potential problem
Richard B Willner
The Center for Peer Review Justice
New Orleans, Louisiana
This is the grand-daddy, unintended consequence of OCare and the EHR mandate. Paper charts reign supreme!
This terrible shit show raises a few questions:
1) What’s the “dark web.” If I’ve been there, I have no idea. I assume the nude photos went from the dark to the light web. Oy.
2) Were the nude photos justified for the treatment of carcinoma? I thought cancers were checked by CT, MR, and PET scans. What was the purpose of the photos if there was no VISIBLE evidence of cancer? Perhaps to document the fields being irradiated…? Does one need to be nude to receive XRT? I simply don’t understand how or why so many cancer patients were photographed in the nude, unless if it was without consent and nefarious.
3) Are the hackers unscathed? Does any of the $65M go to the creeps to prevent further leakage, or can another 160GB of data show up in the future?
To all of my Jewish friends, Shanna Tovah! And have an easy fast.
shana tovah !
As long as there is an ongoing exploitation of hacking both by the hackers as well as the plaintiff attorneys there is never going to be an end of cyber piracy. The society has to decide if it wants to give into cyber piracy making it a lucrative business or to the plaintiffs approached and represented by lawyers knowing that society is at cross roads as to how to tackle this mess of exploitation of the system where there was no intentional harm planned. Someday it will come to hound us all if we will just keep on robbing each others rather than find ac way to handle it sensibly and we all have a stake in this matter.
The individuals whose information was leaked received $50 to $70,000 as Compensation. Did the law firm receive 30+ million dollars?
In my practice all patient photos are stored as hard copy in individual files.
There are several items of consideration here.
1)I do not know who the loss prevention folks are at LVMC, but paying a $5M ransom would have seemed a small price to pay for recovery of penetrated files. Surely the loss prevention people would have realized that they had tremendous upside risk.
2)No amount of hardening and expenses are ever going to keep out hackers. The government needs to step in with more sophisticated tools to interdict these folks, and much faster.
3)I am not sure why the hospital needed nude photos of patients, that were identifiable. This seems odd. I am not sure what purpose they would serve.
4)Where was the AG (state or federal), and were the state police and FBI involved with the ransom request? The state police and FBI would have advised a payout and then would have attempted to capture the crook.
5)I am very surprised that the hospital was judged to be at fault here, as this was the act of an outside criminal. Are the plaintiffs blaming the hospital for not paying ransom? That would seem like a new type of tort. Why are the plaintiffs not going after the hacker and demanding that the government do something.
6)The HITECH act rushed us (through meaningful use government incentives) into a world where the EHR was not ready from a user interface, government interoperability standard, or from a cyber security standard. One has to recall that Microsoft came out with Windows 10 because older operating systems were just not as secure. They are moving to Windows 12 at year end of 2025, for the same reasons. So we are in a world where electronic records are inaccessible without jumping through hoops for patients or family records, but thieves have ready access.
Paper records were slow and cumbersome, but provided far more useful information in far more constrained space than EHRs. Short of a physical breakin to the office, those files were secure.
Now all bets are off.
Anyone caught and convicted of any type crime using the internet in any …(ANY) ! way should get a mandatory 50 years to life in prison.